Secure SE
Fingerprint Authentication PC Security Software
Download
Product Overview: IZZIX Secure Standard Edition is a PC security software for the clients using
the fingerprint authentication technology among the biometrics technologies.
Since the basic PC user authentication is managed by using the fingerprint
authentication information of the user, it is enabled to prevent the release of
password, and keep security of the client PC more effectively from the access
of malicious hacker or outside person.
The functions of file encrypt/decrypt and entire deletion by security folder and
shell enable the user to keep and manage the files in the user’s PC more easily
and effectively.
By using the basic account information of Windows OS as itself and realizing
the OS-friendly user interface through Windows common control, any confusion
or discomfort of the user from installation of new software was minimized.
It supports the domain user function that can be used by installing it for the
client who uses the Active Director of Windows Server System(2003, 2000).
IZZIX Pass UI
Fingerprint Web Log-On Security Software
Download
System Requirements: Microsoft Windows XP/ Windows 7, CPU Pentium 133MHz, Minium 20MB free HDD space, RAM 16MB, USB port, Internet Explorer 5.5
Charateristics:
- IZZIX Pass remembers the log-on information you have used in certain websites by fingerprint authentication and automatically log you on when you revisit them with a single click.
- IZZIX Pass can block flash commercials inserted in many websites that often slow down your Internet speed and even system speed.
- IZZIX Pass blocks annoying pop-up ads and unwanted pop-up windows.
- All Personal data such as log-on, bank account, and fingerprint authentication is backed up and used in other user's requirements.
Fingerex
Fingerprint Authentication Solution Download
 Fingerex developed by Digent is a fast and large capacity fingerprint
authentication server system. And since fingerprint cannot be shared with
others, Fingerex is the sure method for authenticating someone. Fingerex can be
applied to any system without much modification of existing Internet web server
system or application system.
Fingerex developed by Digent is a fast and large capacity fingerprint
authentication server system. And since fingerprint cannot be shared with
others, Fingerex is the sure method for authenticating someone. Fingerex can be
applied to any system without much modification of existing Internet web server
system or application system.
System Requirements:
Client - Windows XP, Windows 7, More that 1GB HDD, Interface USB port, Higher than IE 6.0
Authentication Server - Higher than Windows 2003, Minum RAM 512MB, More than
10GB, Interface Access, MS-SQL, Oracle, DB2 etc. Higher than IE 5.0
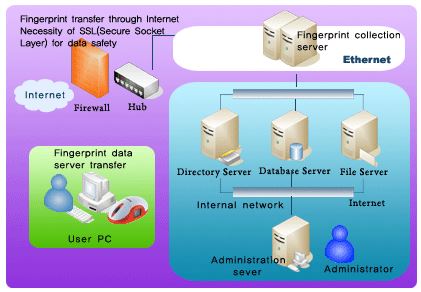
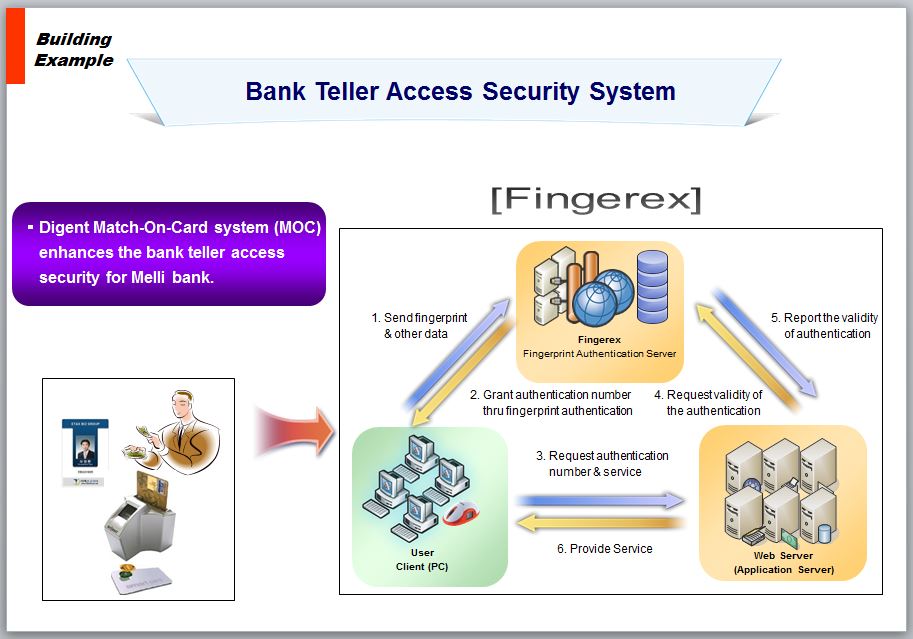
System Structure
The fingerprint feature points transferred from a personal PC is saved in Server Database, LDAP and File System through the fingerprint collection server and the administrator can manage the fingerprint feature points through the administration sever. The fingerprint data is saved in the server after encryption.
Charateristics
Security
- Fingerex system guarantees the complete security because it independently operates.
- When fingerprint data is transferred over the Internet, all data is encrypted.
- With its special triangular fingerprint security architecture, Fingerex is made physically impossible to be hacked.
Stability
- Fingerex system can operate in multiple servers, so that if one server is down, a back-up server from other location can maintain the service.
- If one Fingerex server has the hardware problem, the client PC automatically finds another working Fingerex server.
- Fingerex system does not have limitation on size
- Fingerex system uses non-repeating and one-time password of 64~128bytes, authentication number.
Convenience
- Fingerex system does not have limitation on size
- Fingerex-SD system is equipped with dispersion server, so if the number of hardware is increased, the fingerprint authentication speed goes up.
Flexibility
- It is easy to make any design the user want.
- The user can design as many fingerprint screens as they want.
Application
Documents to be secured or emails transfer, Encryption of a personal file, Important security documents transfer
Fingerex SD
Secure Document System
 Fingerex-SD that is Outlook Add-In developed by Digent is the fingerprint
security email system. Fingerex-SD makes Outlook application allow only the
authorized fingerprint to access the application, and send/read encrypted
emails. Fingerex-SD allows a user to encrypt a document with his or her
fingerprint, so that decryption can be performed by only the same person.
Fingerex-SD can be applied to the existing Microsoft Outlook application without
any modification of the system. Fingerex-SD is an application program based on
Fingerex authentication system.
Fingerex-SD that is Outlook Add-In developed by Digent is the fingerprint
security email system. Fingerex-SD makes Outlook application allow only the
authorized fingerprint to access the application, and send/read encrypted
emails. Fingerex-SD allows a user to encrypt a document with his or her
fingerprint, so that decryption can be performed by only the same person.
Fingerex-SD can be applied to the existing Microsoft Outlook application without
any modification of the system. Fingerex-SD is an application program based on
Fingerex authentication system.
System Requirements: Authentication Server - When using Fingerex-SD Server &
Manager, the following items are essential. Install Microsoft Explore 6.0
Service Pack 1 or higher and Microsoft MS-SQL 2000 Service Pack 3 or higher
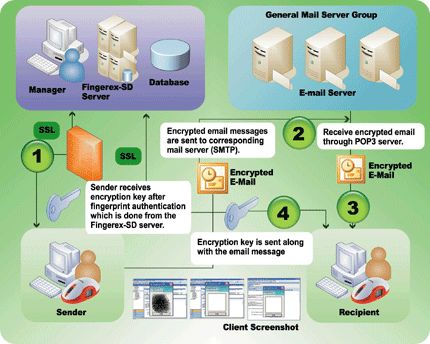
System Structure:
- After accessing to Fingerex-SD server by fingerprint authentication, the
sender receives the authenticated user's encryption key in DB.
- The e-mail encrypted by the user's encryption key is sent to the mail server
(SMTP).
- The sequence of decrypting an e-mail by the sender's fingerprint
authentication
1. Receiving an e-mail (encryption) from the server
2. Authenticating through Fingerex-SD server
3. Receiving the encryption key after success of authentication
4. Decrypting the e-mail by using the received encryption key
Security
Application: Securing documents or sending/receiving security e-mails
Charateristics::
Security
- Fingerex system guarantees the complete security because it independently
operates.
- When fingerprint data is transferred over the Internet, all data is encrypted.
- Fingerex-SD system relies on unique fingerprint authentication structure and
encryption to protect this fingerprint data from physical hacking.
- Only the designated recipients can decrypt the encrypted document after
fingerprint authentication.
Stability
- Fingerex-SD system can operate in multiple servers; thus, if one server is
down, a back up server from other location can maintain the service.
- Fingerex-SD system allows only those users, authorized by fingerprint
authentication, to access Outlook, and to read encrypted email.
- SD system uses HYH file extension, so even though HYH file extension is used,
SD system analyzes a file when opening the e-mail and checks if the mail is from
SD system.
Scalability
- Fingerex-SD system does not have limitation on size
- Fingerex-SD system is equipped with dispersion server, so if the number of
hardware is increased, the speed of fingerprint authentication goes up.
Convenience
- Fingerex-SD supports Outlook or Outlook Express and is compatible with them.
- Fingerex-SD minimizes the size of email by encrypting and compressing it at
the same time when sending it out.
- Fingerex-SD has its own address book
Flexibility
- Fingerex-SD can register 10 different fingerprints.
Secure Pro
Centralized Fingerprint User Management Solution
 System Requirements:
Microsoft Windows7/XP, CPU Pentium 133M, 64MB RAM, USB Port 1.0, CD-ROM Drive
System Requirements:
Microsoft Windows7/XP, CPU Pentium 133M, 64MB RAM, USB Port 1.0, CD-ROM Drive
Charateristics:
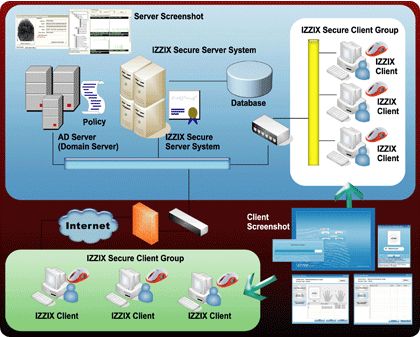
- Domain logon function
- Domain user supports log-on function for all clients by one time registration
of IZZIX-Secure Pro.
- Domain user management through IZZIX Secure Pro Manager (user information,
fingerprint etc.)
- Client user management through IZZIX Secure Pro Manager (user information,
fingerprint etc.)
- Selection/deselection of security files (Drag-AND-Drop method)
- Password filter function in Domain server PC and Client PC (When changing
user's password, the password in IZZIX-Secure Pro automatically changes)
- Fingerprint is compatible with ID&P/W based on AD (Active Directory), when
logging on AD
- Domain from a client's PC with Windows Server OS Fingerprint log-on function
including the base AD function
- Examining the user's system health by supporting system monitoring function
- Easy parallel distributed processing and scalability through NET Web service
- Extension of the number of user fingerprint including IZZIZ Secure client
function
- Easy to encrypt and decrypt a file through the security folder function

We continuously make an effort to become a top leader in a finger biometric field.
| Type | Model Number | Solution | Sample |
|---|---|---|---|
| Hardware | IZZIX FM1000 | Fingerprint identification optical mouse (USB Interface) | Info |
| Hardware | IZZIX FD1000 | Fingerprint identification scanner. Stand-alone type (USB Interface) | Info |
| Hardware | IZZIX FD2000 | Fingerprint identification scanner. Stand-alone type (USB Interface) | Info |
| Hardware | IZZIX FD4000 | Fingerprint identification scanner. Stand-alone type (USB Interface) | Info |
| Hardware | IZZIX DuoPASS | Fingerprint identification scanner. Access control | Info |
| Hardware | IZZIX CB1000 | A combined smartcard and fingerprint identification. Dummy scanner (USB Interface) | Info |
| Hardware | IZZIX FC20 | Fingerprint identification logger (USB Interface) | Info |
| Software | IZZIX Secure | Fingerprint identification PC security program for clients | Info |
| Software | IZZIX Secure Server Pro | Fingerprint identification security Package Program | Info |
| Software | Fingerex | Internet, Intranet, TCP/IP-based. Fingerprint authentication server solution | Info |
| Software | Fingerex SD | Internet, Intranet, TCP/IP-based. Fingerprint authentication e-mail security solution | Info |
| Software | IZZIX Pass | Auto-filled function utility for fingerprint authentication website ID&PW and other information | Info |

Application developers: Anyone who develops an application for user administration and authentication can use IZZIX SDK with ease to build a fingerprint-based authentication for custom applications.
IZZIX SDK composition supplies everything that is needed to develop applications that use IZZIX fingerprint authentication technology. This SDK includes hardware driver for fingerprint authentication device, Header file defining the Finger API, library Visual C++ 6.0 sample code and the fingerprint algorithm. The SDK allows a developer to develop applications that authenticate fingerprint in real-time.
IZZIX Fingerprint Recognition Algorithm follows the commonly accepted fingerprint identification scheme, which uses a set of specific fingerprint feature points (minutiae). In addition, it contains many advanced algorithm solutions, which enhance the system performance and reliability.
Fingerprint image check algorithm: This algorithm makes sure the quality of the fingerprint and possibility to use the fingerprint. It checks error codes such as incorrect image position (up, down, left, and right), no fingerprint present or fingerprint too dry or too wet.
Fingerprint image enhancement algorithm: This algorithm allows to eliminate injuries, ridge ruptures and stuck ridges, and selects feature points more reliably even from poor fingerprint images with processing time of 0.2~0.3 seconds on a Pentium 200. Because there can be many distortion, translation, and rotation in fingerprint image caused by various reasons, this algorithm selects feature points of fingerprint. IZZIX fingerprint algorithm is fully tolerant to them. IZZIX fingerprint algorithm uses a fingerprint matching, which can match 12000 fingerprints per second and identifies fingerprints even if they are arbitrarily rotated within 360°. And then, this algorithm is not depended on the presence of the fingerprint core or delta points in the image.
Fingerprint enroll using feature collection mode: IZZIX fingerprint algorithm can register fingerprint by using feature points collection mode. When using this mode, the same fingerprint of a user is scanned 3 times and the scanned fingerprint images are processed separately to select feature points from each image. And after finding the common feature points from three images, the common feature points are saved in the database. The fingerprint data processed by this procedure is more confident and efficient than other fingerprint data.
Database pre-sorting using global feature data: IZZIX Fingerprint algorithm sorts and saves each data incoming to the database by the easiest distinguishable features. Fingerprint matching is performed first with the pre-sorting data by global feature, and then more detailed feature is matched with the fingerprint data in database until the correct match is found. In most cases, the correct match is found in the beginning of the search and IZZIX fingerprint algorithm quickly finds the matching fingerprint even the huge database.
Algorithm for 1:1 and 1:N matching: IZZIX fingerprint algorithm can match 1:1 and 1:N.
Security and privacy: SDK is very excellent for security and privacy. A user's fingerprint templates can be returned by encryption type from fingerprint algorithm and are saved in the database by encryption type. The encrypted fingerprint data can be used by the decryption method used internally and it is impossible to match fingerprint in the database by using the saved fingerprint. In addition, SDK does not provide any function related to encryption and decryption.
Specification:
- Fingerprint Enrollment Speed 0.2 seconds
- Fingerprint Authentication Speed 12000 prints / second
- Fingerprint Template Size 480 bytes
- Fingerprint Rotation Range 0°~360°
- Matching Security Level 5 levels
- False Rejection Rate (FRR) ≤1%
- False Acceptance Rate (FAR) ≤0.0001%
System Requirements:?
This content area will be showing main summary. This is a test. If you have any question please let us know. This content area will be showing main summary. This is a test. If you have any question please let us know. This content area will be showing main summary. This is a test. If you have any question please let us know. This content area will be showing main summary. This is a test. If you have any question please let us know. This content area will be showing main summary. This is a test. If you have any question please let us know. This content area will be showing main summary. This is a test. If you have any question please let us know.This content area will be showing main summary. This is a test. If you have any question please let us know.This content area will be showing main summary. This is a test. If you have any question please let us know.
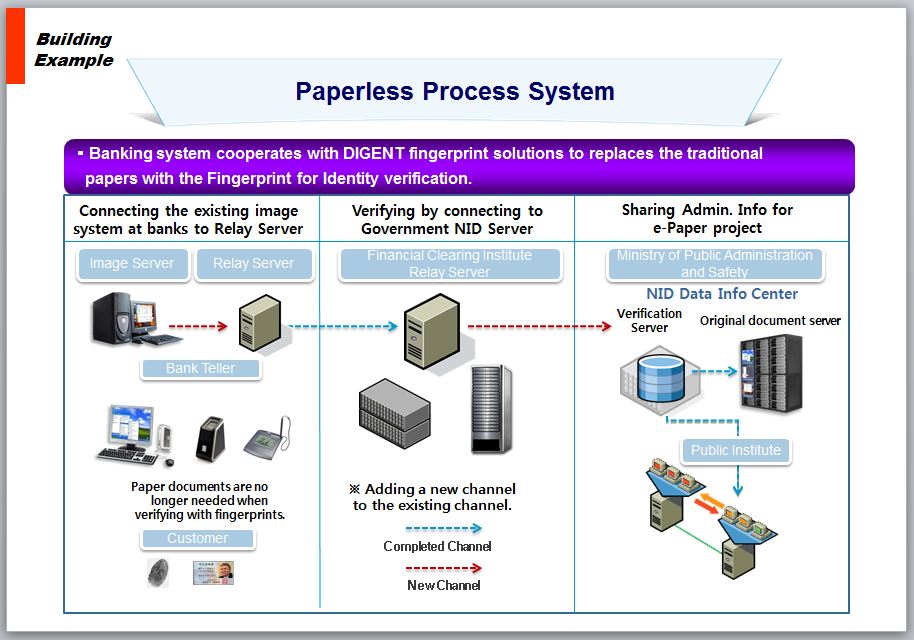
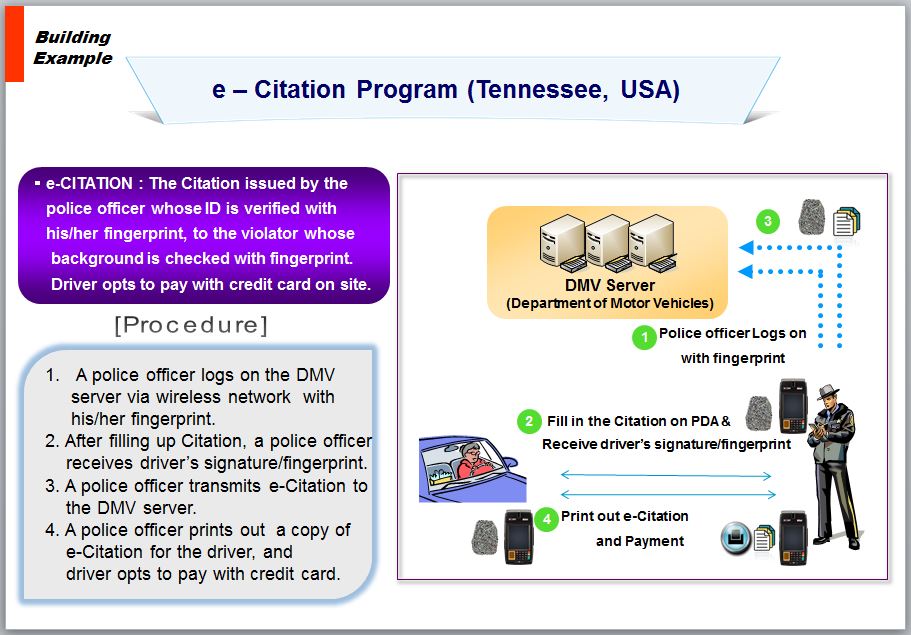
E-Citation Program in Tennessee, USA (Police Department)
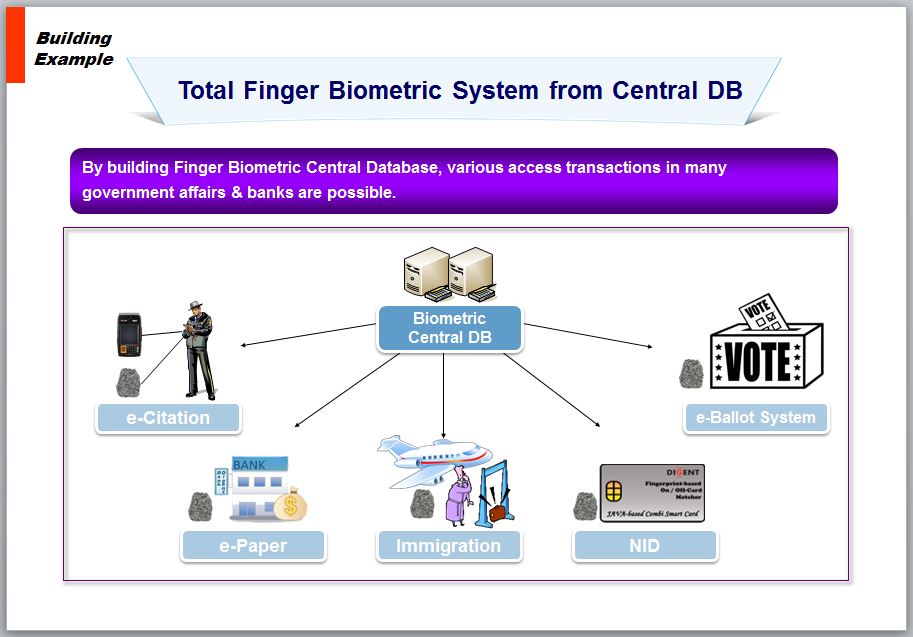
Total Finger Biometric System from Central DB
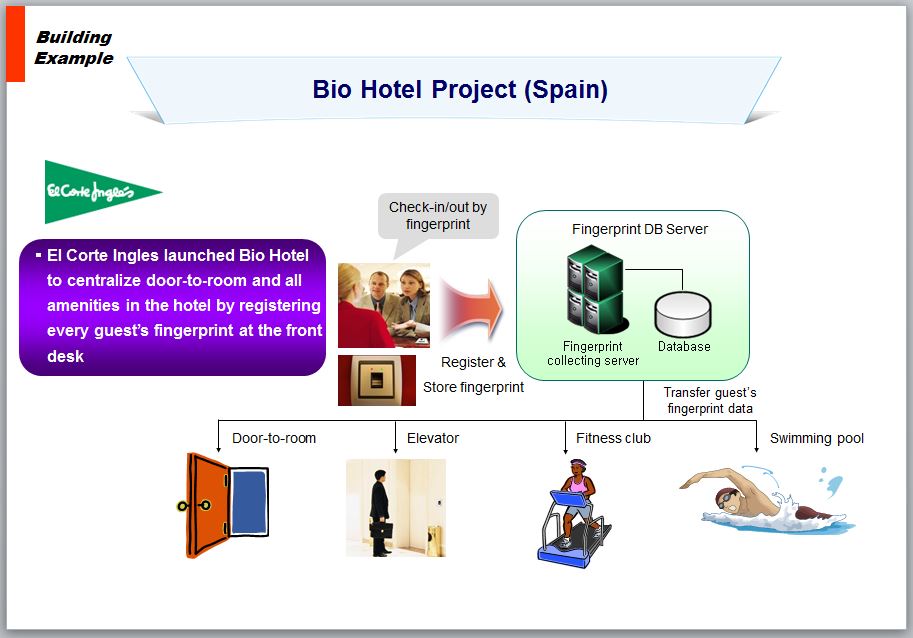
Environment Friendly System: Saving $270 Million Dollars including cost of papers, printing, copying, storing, delivering, and Reducing the CO2 Emission total 193,920 tons of CO2 from papers 55,755 tons and distribution 138,165 tons.